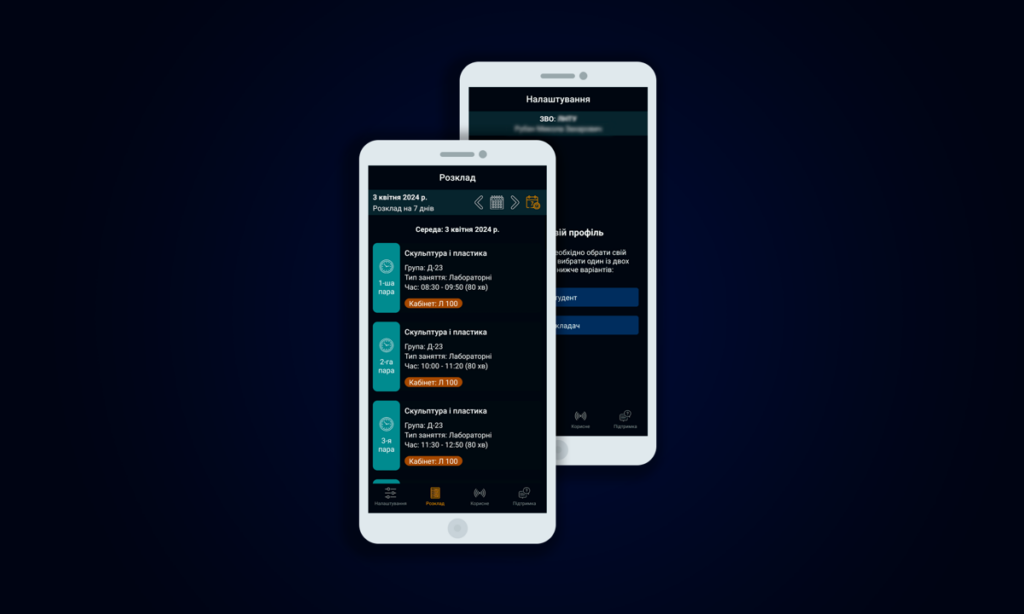
Mission.
To improve the efficiency of management of Ukrainian educational institutions using modern information technologies, and thus to facilitate the creation of a single information space for management activities.

Professionalism
We consider the professional experience and technical competence of our specialists, recognised by our clients and confirmed by a large number of awards, to be of particular value.

Innovations
We offer solutions that ensure a qualitative increase in the efficiency of management activities in the education sector.
Responsibility
Our company believes it is important and necessary to participate in the informatisation of the Ukrainian education system.
About the company
The determining factor of the company's leadership in the domestic IT market is the dedicated work of a highly professional team of the best domestic IT specialists. The company's management creates all conditions for employees to improve their skills, acquire the necessary knowledge and skills required for successful professional activities.
Partner organisations